What’s a secret?
That’s a good question. But if you’re here, you probably already understand what a secret is, with regards to software engineering. You also understand that once code has been merged, detecting and fixing security related defects in code can cost your business time, money, and expose your organization to security risks. And the later in the lifecycle these issues are detected, the more costly the issue can be. Because of this, the best way to help developers keep secrets and passwords out of code is to shift security left.
But what does that mean?
Shifting security left means to move security to the earliest possible point in the development process and integrate it directly into your developers’ daily development workflow. By doing so, developers can catch security issues before they are even committed into the repository.
How do you do this?
You empower developers with the right tools.
Fortunately, there are plenty of options perfectly suited to help you shift security left.
Let’s take a look at two very important tools for this task.
BluBracket Community Edition
BluBracket Community Edition helps developers and security professionals in two ways. One it provides a CLI tool that developers can integrate with their IDE, so it will check and flag secrets pre-commit. This is crucial because once a secret is committed into a repository, it’s extremely difficult to get it out without rewriting the whole repository.
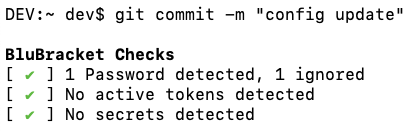
BluBracket also allows developers to scan the entire history of all commits in their repositories and aggregates the overall risk of a repository via a Repo Risk Score so security engineers could work towards a path of remediating the risks.
BluBracket Community Edition is capable of catching the following types of secrets:
- AWS
- Slack
- GitHub
- GitLab
- Azure
- GCP
- Passwords
- Credentials
- Environment and other sensitive type files
- and 55 more secret types.
BluBracket uses regular expressions and the hyperscan library, which creates a bounding box of anything that could be considered of interest, before running an even deeper analysis. The tool allows you to build a .bluebracket-ignore file to exclude files, or secret types to filter out false positives.
Now let’s say that the CLI has discovered secrets and blocked the commit containing secrets from getting into the repository – what is the alternative to storing secrets directly in code?
Instead of referencing the secret directly in the code a developer should fetch the secret from a secrets manager.
Say, for example, you have a password that is required to connect code to a service or API. Instead of referencing the password directly in the code like this
password = My$3cr3tP@$$W0rD
You’d instead integrate with a secret manager (such as Hashicorp Vault.) For example, if you want to use Vault for that integration the code might then look like:
import hvac
vault_client = hvac.Client(url=’https://vault.acme.com:8200‘, token=os.environ[‘VAULT_TOKEN’],)
# Assumes the password is stored with key value in kv v2 secrets engine mounted at my-mount-point/
secret_data = vault_client.secrets.kv.read_secret_version(path=’MyPasswordPathInVault’, mount_point=’my-mount-point’)
password = secret_data[‘data’][‘data’][‘value’]
As you can see above, we’ve migrated away from storing actual passwords in the code, to connecting to a third-party secrets manager. The password is no longer visible within the code, so it’s far more secure.
Vault
Vault is a platform-independent secrets manager that allows developers to secure, store, and tightly control access to tokens, passwords, certificates, encryption keys, and other sensitive information. With a user-friendly UI and a powerful CLI, you can easily shift from a static infrastructure approach (on high-trust networks, a clear network perimeter, and IP address-enforced security) to a dynamic infrastructure (on low-trust networks in public clouds, unknown network perimeters across clouds, and security enforced by identity) without having to risk your secrets.
Vault is API-driven with support for AWS, Microsoft Azure, Google Cloud, okta, Alibaba Cloud, SSH, Kubernetes, and GitHub.
Vault also integrates with the following databases MySQL, Cassandra, Oracle, AWS, mongoDB, HashiCorp Consul, Microsoft SQLServer, PostgreSQL, and Microsoft Azure.
Vault can be installed on FreeBSD, Linux, macOS, NetBSD, OpenBSD, Solaris, and Windows.
In this day of CICD and cloud native development, it’s absolutely crucial that you do everything you can to shift your security left. By making this change, you ensure that vulnerabilities in code (such as exposed secrets) are not only found earlier in the dev lifecycle, but never enter the code repository to begin with.


